Configuration Example
Here’s an example of how to configure NPS to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’.
This is a RADIUS attribute that may be passed back to the authenticator (i.e. the WLC or AP) by the authentication server (i.e.NPS) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by NPS are:
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
- Tunnel-PVT-Group-ID: <VLAN Number>
We’ll have a look at how we specify each of these attributes in an NPS policy.
For our example, we’ll assign all ‘staff’ users to VLAN 10 and all ‘student’ users to VLAN 20.
Here is an overview of what the network might look like (this is obviously very simplified, but gives an overview of the type of thing that might be achieved):
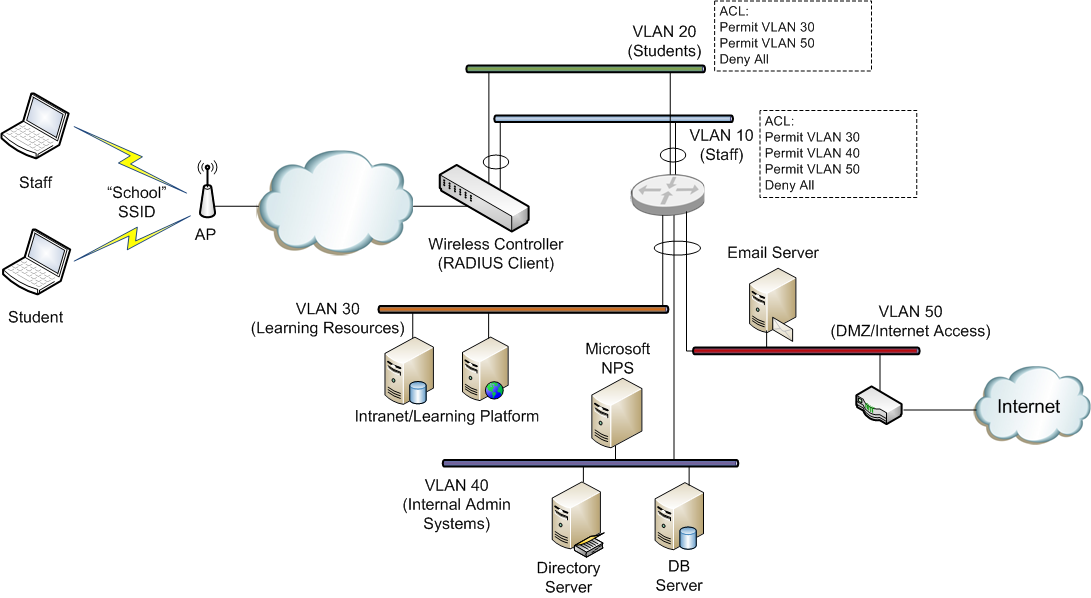
VLAN 10 has an ACL (access control list) that allows users on this VLAN to access all systems across the school network. The ACL would generally be configured on the layer 3 switch or router that interconnects the school VLANs)
VLAN 20 has an ACL which only allow access to the learning system VLAN and the Internet related services.
By studying the example above, you can see that if we can control a users VLAN assignment, based on their AD group membership, we can ensure that they only receive the network access to which they are entitled (purely via their AD group membership). Also, note that this is all being done on a single SSID (“School” in this case).
Now we’ll take a look at how we achieve this using NPS.
NPS Configuration
To configure NPS to provide the VLAN assignments outlined above, we will create 2 policies within NPS:
- School Wireless – Staff (to assigned members of the staff AD group to VLAN 10)
- School Wireless – Students (to assign members of the students AD group to VLAN 20)
The screen-shots below outline the configuration required. Here is the policy summary screen within NPS. Note that when configuring multiple policies, the order of the policies is important. Policies are assessed top-down, so make sure the policies that need to be hit are enabled and above any disabled polices.
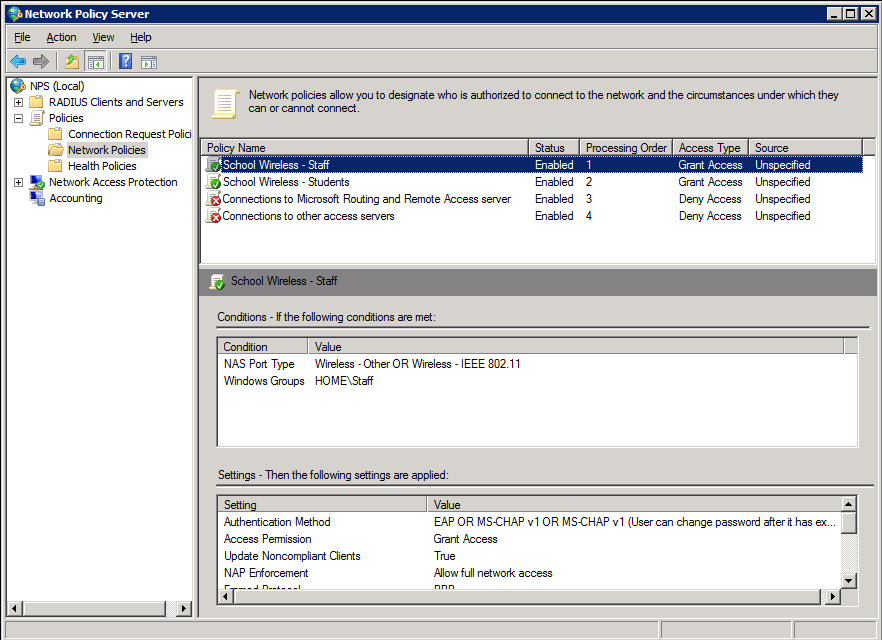
Staff Policy
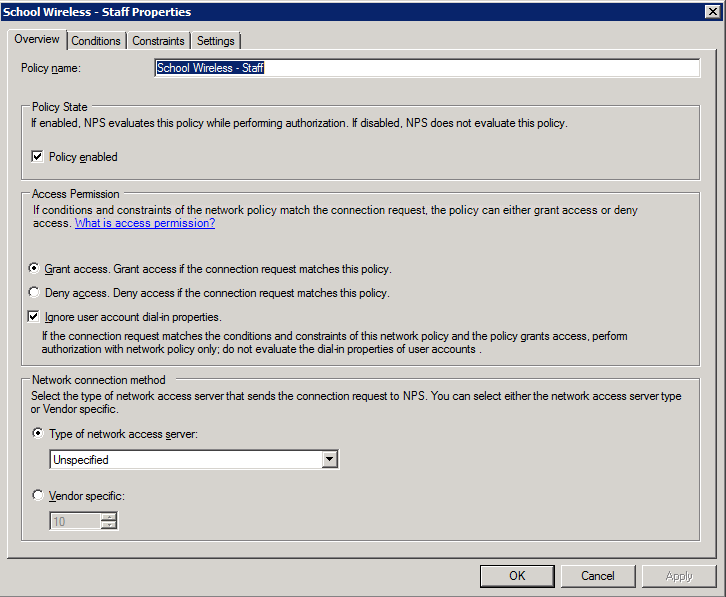
1. Create the policy and enable it:
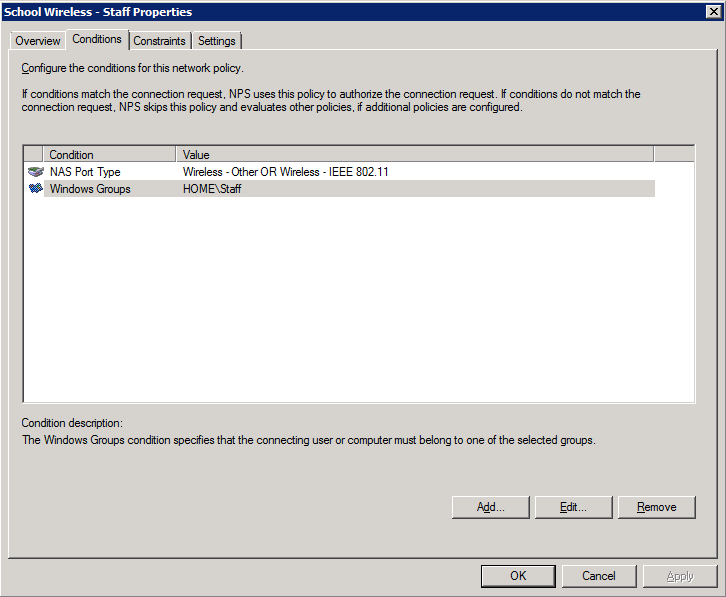
2. Add the NAS type and AD group membership conditions (must be members of the staff group):
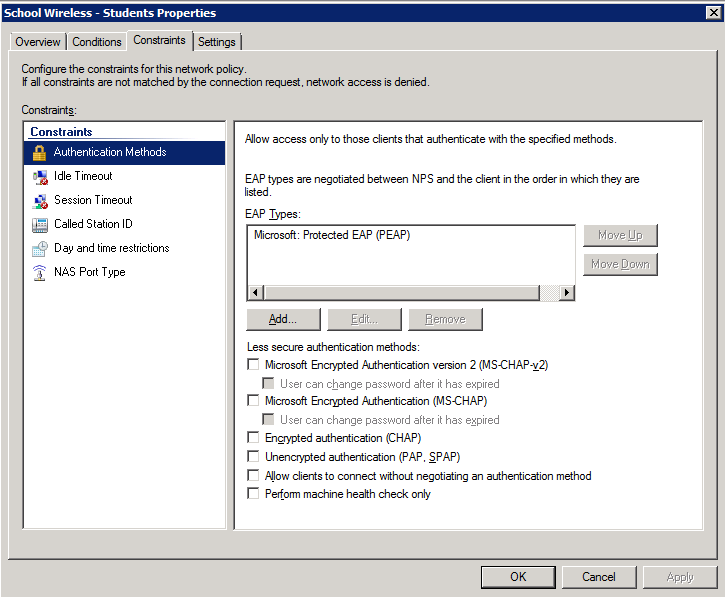
3. Select and configure an EAP type (note this may be PEAP or EAP-TLS – we’ve shown PEAP just as an example)
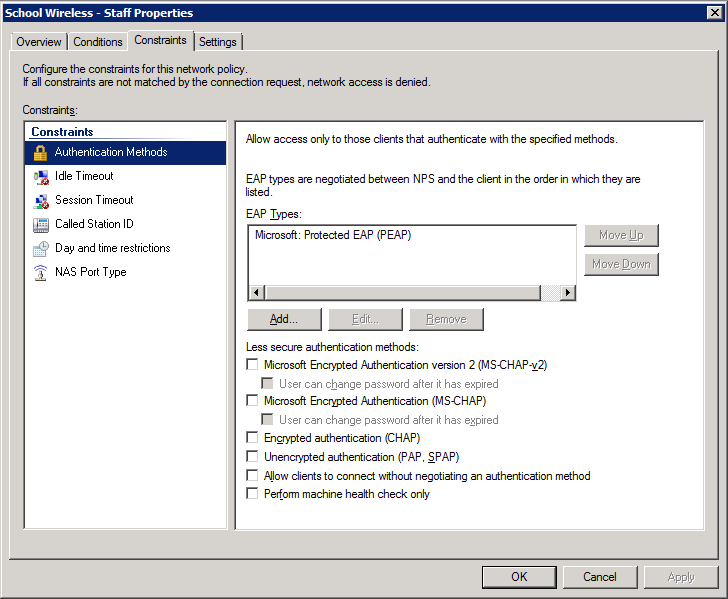
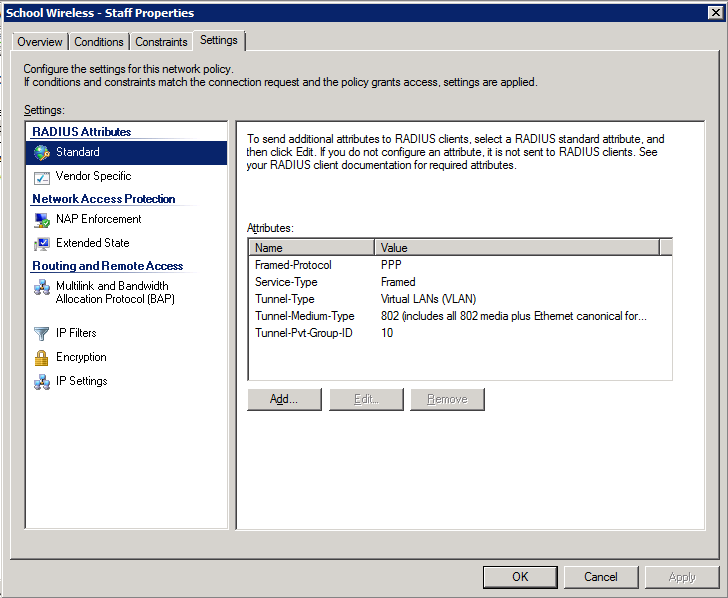
4. Configure the settings for this policy to assign any users which match this policy to VLAN 10:
Students Policy
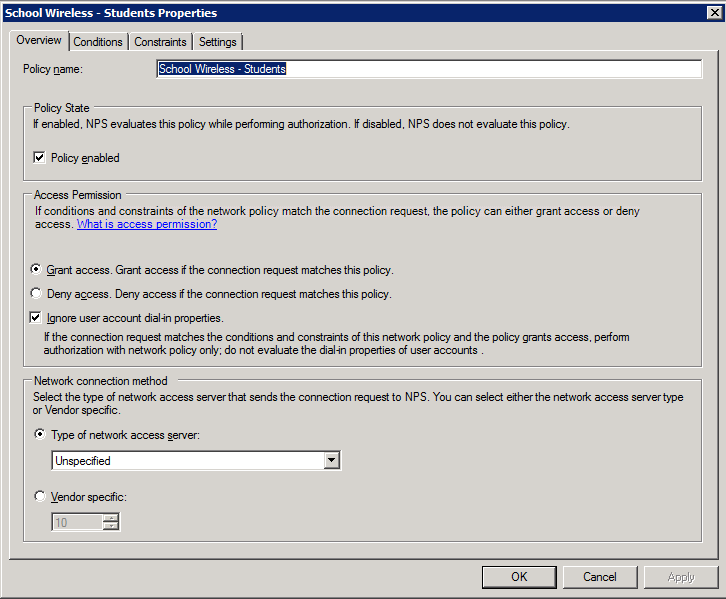
1. Create the policy and enable it:
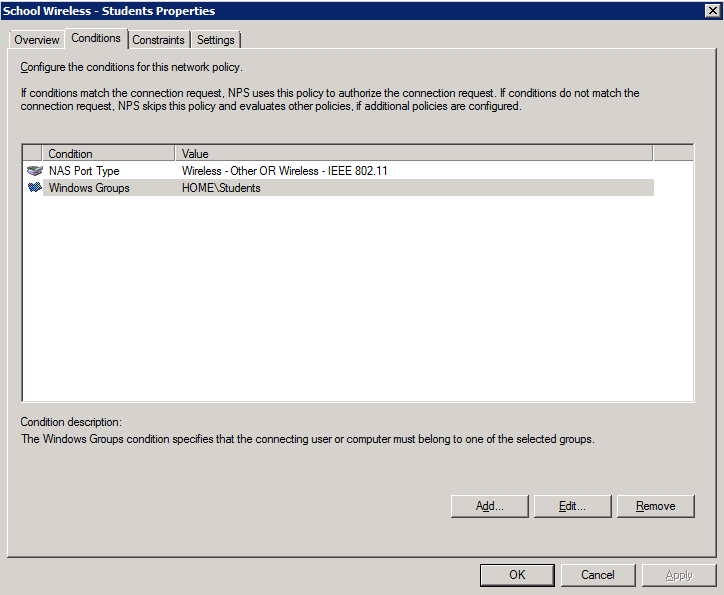
2. Add the NAS type and AD group membership conditions: (must be members of the students group to match this policy)
3. Select and configure an EAP type (note this may be PEAP or EAP-TLS – we’ve shown PEAP just as an example)
4. Configure the settings for this policy to assign any users which match this policy to VLAN 20:
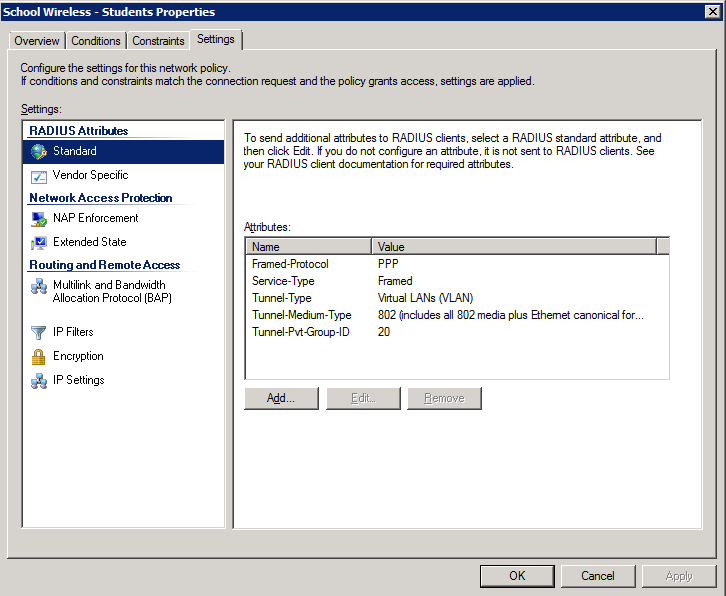
Once NPS has been configured with policies similar to those shown above, users can be dynamically assigned to an appropriate VLAN based on their AD group membership.
As we’ve already discussed, this provides great benefits in reducing additional overheads associated with multiple SSIDs on a WiFi network. In addition, it simplifies user wireless management by allowing all users to be configured with a single wireless client profile, with their access being configured via Microsoft AD.
One caveat to note when trying to use this technique is that all users must be using the same security mechanisms to join the SSID. For instance, all users must be using 802.1x (EAP) – you can’t have a mix of PSK & 802.1x authenticated devices on the same SSID. Generally, they should also be using the same WPA version (i.e. WPA or WPA2).
